Data Protection and Security
Our clients place their trust in our systems and we make it our highest priority to keep their data secure.
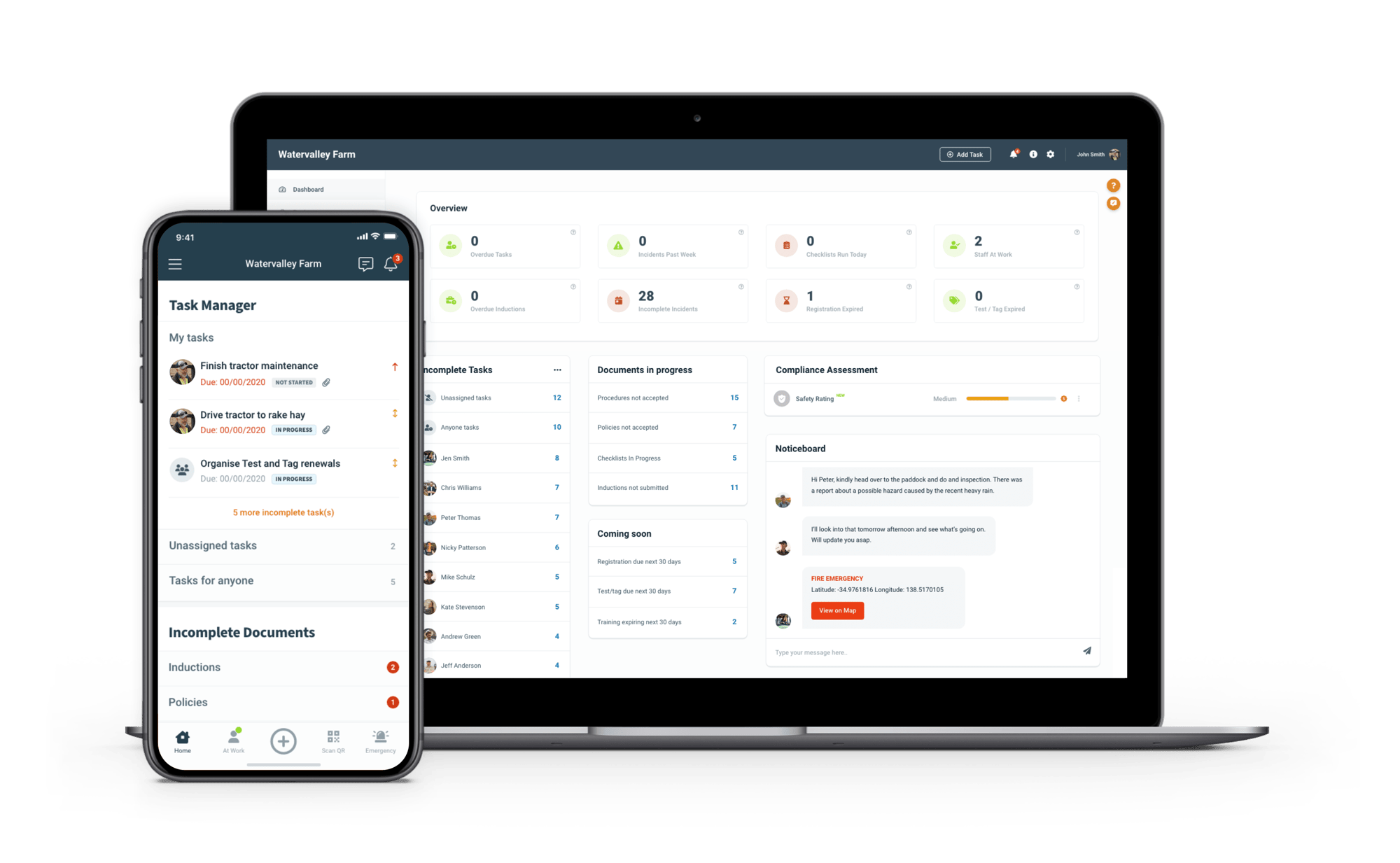
At Safe Ag Systems, we take your Data Privacy seriously
Our cloud-based health and safety management system utilizes data encryption methods, and industry-standard security software and methodologies. Your data is also protected with your unique authentication credentials as well as access control ensuring the protection of your records.
Our website is Secure Socket Layer (SSL) encrypted, ensuring data processed remains secure. SSL technology makes an internet connection secure and safeguards any sensitive data that is being exchanged between two systems, preventing criminals from reading and modifying any information transferred, including potential personal details.
Our clients trust us to ensure the security and confidentiality of their information. Our providers utilise Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform employing world-class cloud infrastructure. Providers are SOC 2 Type II and ISO 27001 certified. ISO27001 is a global standard for the management of information security. A SOC 2 Type 2 is an internal controls report capturing how a company safeguards customer data and how well those controls are operating.
Personal data is protected using the appropriate physical, technical and organisational security measures. Where applicable, we provide additional attention to sensitive personal data and respect local laws and customs. We are committed to protecting personal data and we implement the appropriate technical and organizational security measures. You retain ownership of data you enter and upload into your system. Safe Ag Systems only utilises this data to provide you with our services. Information is processed for the purpose in which it was collected or authorised in accordance with our privacy policy.
Safe Ag Systems Cyber Security Measures in Place:
Learn more about the control measures Safe Ag Systems implement in our daily operations.
Cyber Security Insurance
The policy includes Technology Liability protection and Cyber protection.
-
Incident Response
-
Business Interruption
-
Data and System Recovery
-
Cyber Extortion
Network Security
Firewall in Place
-
Deep Packet Inspection
-
Encrypted Traffic
-
Zero-Day and ML Protection
-
Web Protection
-
Advanced Threat Protection
-
Application Control
-
User Identity
Corporate Security
-
Employee Cyber Awareness Training
-
Data Protection Training
Endpoint Security
-
Device Encryption Policy
-
Application Control Policy
-
Data Loss Prevention
-
Windows Firewall
-
Peripheral Control
-
Threat Protection
-
Update Management
-
Web Control
-
VPN for Remote Workers
-
Microsoft Intune Device Management
Data Security
-
Daily backups with Veeam
-
Access Control in Place
-
Multi-Factor Authentication is Enforced
-
Employees store their passwords in a company-controlled password manager
-
Physical Security: Office building has a key card door lock system, security cameras and motion sensors.
Policies
- Information Security Policy
- Acceptable IT and Internet Use Policy
- Password Policy
- Confidentiality Policy
- Working From Home Policy
- Cyber Security Incident Reporting Policy
- Acceptable use of Assets Policy
- Encryption and Cryptographic Controls Policy
Reports
-
Cyber Security Incident Reporting
-
Data Breach Response Plan
-
Disaster Recovery Plan
-
Network Diagram
-
Penetration Test Report
Compliance
- Working Towards GDPR Compliance
- Gained ISO27001 Certification
- Participating in the partnership program of the Australian Cyber Security Centre
Looking for more information?
.jpg?width=2000&name=www.safeagsystems.comhubfsfarm%20cyber%20security%20(2).jpg)
Cyber safety for agricultural businesses
We are committed to protecting personal data, implementing appropriate technical and organizational security measures.
Read More.jpg?width=1920&height=1280&name=Cyber%20security%20blog%20(2).jpg)
Stay cybersafe and recognise if you've been hacked
Be aware of suspicious behaviours happening on your accounts, devices and apps. There are multiple warning signs.
Read More
Check out our cybersecurity checklist
Securely organizing your software can increase your business’ protection. See our top 4 tips to stay cybersafe.
Read MoreProduct
Resources
Our Company
Copyright 2026. Safe Ag Systems
- Privacy Policy
- Terms and Conditions
- Data Protection & Security








